- 마이크로소프트가 패브릭 내에서 데이터와 AI를 통합하는 이유
- 레드햇, AI 포트폴리오 대규모 업데이트…엔터프라이즈 배포 유연성 확대
- I recommend this cordless stick vacuum over my Dyson - and it's on sale
- I tested a smart cooler and can never go back to toting ice (especially for $100 off)
- This wireless portable speaker delivers amazingly smooth sound with little distortion
Microsoft’s January 2021 Patch Tuesday Addresses 83 CVEs

In its first Patch Tuesday of 2021, Microsoft patched 83 CVEs including 10 critical vulnerabilities
Microsoft patched 83 CVEs in the January 2021 Patch Tuesday release, including 10 CVEs rated as critical and 73 rated as important.
Compared to Microsoft’s January 2020 Patch Tuesday release, which included fixes for 49 CVEs, this represents a 69% increase in CVEs patched. If that’s any indication, it means 2021 will be another banner year for Patch Tuesday vulnerability disclosures.
This month’s Patch Tuesday release includes fixes for Microsoft Windows, Microsoft Edge (EdgeHTML-based), Microsoft Office and Microsoft Office Services and Web Apps, Microsoft Windows Codecs Library, Visual Studio, SQL Server, Microsoft Malware Protection Engine, .NET Core, .NET Repository, ASP .NET and Azure.
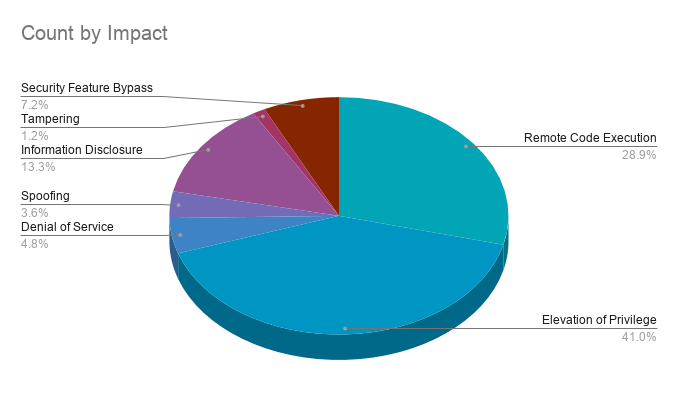
Elevation of privilege vulnerabilities accounted for 41% of the vulnerabilities patched this month, followed by remote code execution (RCE) flaws at nearly 29%.
CVE-2021-1647 | Microsoft Defender Remote Code Execution Vulnerability
CVE-2021-1647 is an RCE vulnerability in Microsoft Defender, Microsoft’s flagship antivirus and antispyware solution. The vulnerability exists within the Microsoft Malware Protection Engine, a core component of Microsoft Defender that addresses malicious software. According to Microsoft, CVE-2021-1647 was exploited in the wild as a zero-day. Details about the in-the-wild exploitation are not yet known. However, considering Microsoft Defender enjoys a 50% market share that represents over 500 million systems worldwide, it provides attackers with a significant attack surface.
CVE-2021-1648 | Microsoft splwow64 Elevation of Privilege Vulnerability
CVE-2021-1648 is an out-of-bounds (OOB) read vulnerability in Microsoft’s printer driver host, splwow64.exe. The flaw exists due to improper validation of user-supplied data. According to Maddie Stone, a researcher at Google Project Zero credited with identifying this vulnerability, CVE-2021-1648 is a patch bypass for CVE-2020-0986, which was exploited in the wild as a zero-day.
Microsoft initially planned to patch this vulnerability as part of its November and December 2020 Patch Tuesday releases under a CVE identifier of CVE-2020-17008. However, due to testing issues, it was pushed back to January 2021. Because it slipped into 2021, Microsoft scrapped CVE-2020-17008 and now identifies it as CVE-2021-1648.
Successful exploitation would allow an attacker to read data outside of an allocated buffer, access that could be leveraged to elevate privileges and, if chained with other vulnerabilities, could result in arbitrary code execution on the vulnerable system in the context of the current user. This could result in a complete takeover of the system if the current user has administrative permissions. In addition to Stone, this vulnerability is credited to Elliot Cao via Trend Micro’s Zero Day Initiative, and k0shl of Qihoo 360’s Vulcan Team.
CVE-2021-1674 | Windows Remote Desktop Protocol Core Security Feature Bypass Vulnerability
CVE-2021-1674 is a security feature bypass vulnerability in Windows Remote Desktop Protocol (RDP) which can be exploited by an attacker with a low-level privileged account and network access. The flaw has not been publicly disclosed or exploited, however RDP has been a favored entry point for ransomware actors in 2020 and this trend is likely to continue in 2021.
CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700 and CVE-2021-1701 | Remote Procedure Call Runtime Remote Code Execution Vulnerability
CVE-2021-1658, CVE-2021-1660, CVE-2021-1664, CVE-2021-1666, CVE-2021-1667, CVE-2021-1671, CVE-2021-1673, CVE-2021-1700 and CVE-2021-1701 are RCE vulnerabilities in the remote procedure call (RPC) runtime in Windows. All nine of the CVEs received CVSSv3 scores of 8.8 and were reported to Microsoft by Yuki Chen, head of 360 Vulnerability Research Group and 360 Vulcan team. Microsoft assesses that exploitation is less likely for these flaws, based on the CVSSv3 score, an attacker would need network access and a low privileged account in order to exploit the vulnerability.
Flash Player End of Life (EOL)
Adobe announced that support for Flash Player ended after December 31, 2020 and that Adobe will begin blocking Flash content from running in Flash Player beginning on January 12. Flash’s history of security vulnerabilities spans more than a decade and has been a popular avenue for attackers. While an end to this popular attack vector is welcome news, we anticipate attackers will continue to find new and creative attack vectors in other popular and widely used applications.
Tenable solutions
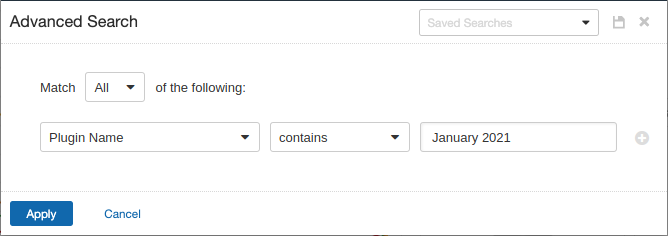
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains January 2021.
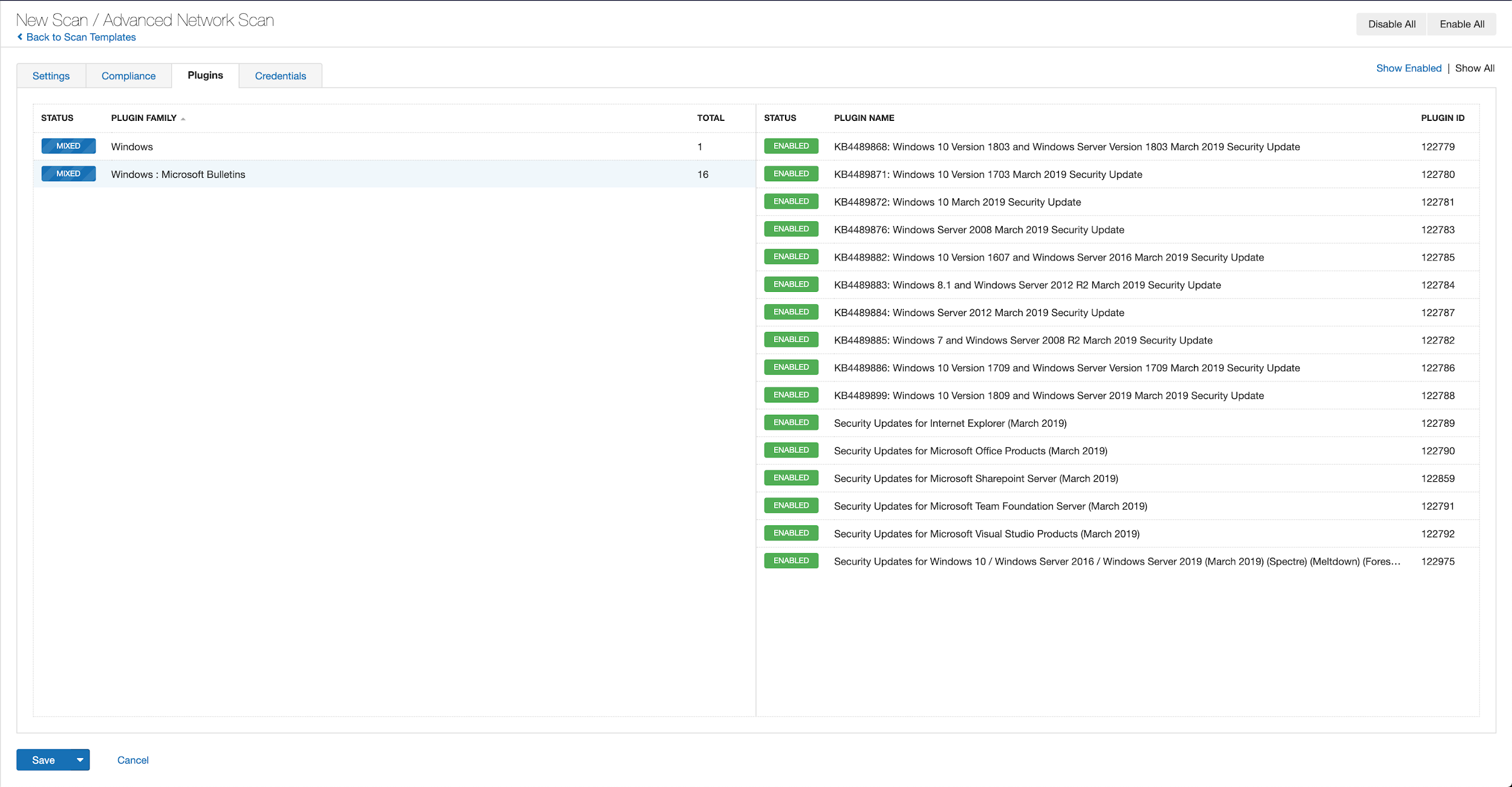
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from March 2019 using Tenable.io:
A list of all the plugins released for Tenable’s January 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Additionally, you can use plugin ID 59196 to identify systems that have Adobe Flash Player installed now that it has reached its end of life and is no longer supported by Adobe.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

